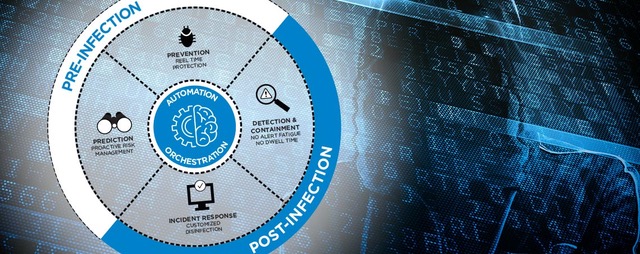
Next-generation EDR antivirus
Protect your business with the latest generation EDR (Endpoint Detection and Response) antivirus software. Unlike traditional static signature detection antivirus no longer able to effectively counter the most recent attacks, EDR solutions analyzes behavior through artificial intelligence (AI) algorithms. “Zero-day” attacks (still unknown today) will be detected by the very responsive EDR, immediately recognizing the virus’ unusual behavior.
EDR Protection against :
- Ransomware
- ZERO DAY Attacks
- Human piracy
- Virus
- Malware
- Advanced persistent threats
Comparison of the most popular EDR solutions
| SentinelOne | Microsoft Defender | CrowdStrike | |
|---|---|---|---|
| Deployment | Federated and Multi-Tenanted Rigorously tested for critical environments. Battle-hardened and built for redundancy. Multi-tenanted by design, with full control over deployment cadence and fewer updates needed. |
Complex and Fragmented Multiple consoles, lengthy setup process, and cumbersome to operate. Limited coverage for operating systems (even Microsoft’s own) creates operational nightmares. |
Single-Point-of-Failure Architecture Cloud dependent, centralized architecture that requires constant updates to remain effective. Poor release management and quality control. |
| Performance | #1 Ranked, Real-Time and Autonomous 100% protection and detection with real-world deployments and the industry’s lowest signal-to-noise ratio, so you can stay focused on what’s most critical. |
Inconsistent and Reactive A scan-based approach leads to high resource consumption, which slows down device operations and creates detection delays. The platform’s reactive nature results in a higher signal-to-noise ratio, making it harder to focus on critical issues especially given the confusing UI. |
Reactive, Visibility-Based Human Response Unless you stay up-to-date with frequent updates and configuration changes, Falcon is ineffective and creates noise—making it hard to respond fast and surface key insights while forcing you to rely more on services. |
| Platform | Unified Data Lake Gives You Flexibility Bring all your data together in a single place. Ingest and normalize data from first- and third-party sources into a centralized Data Lake. Leverage AI SIEM to drive real-time streaming data and Hyperautomation to maximize the value of your investment. |
Disconnected Data Management Data is often spread across multiple tools and consoles, making integration and unified visibility challenging. Limited flexibility in data ingestion and higher costs for first-party data usage can hinder comprehensive data management and analysis. The single vendor approach also increases risk significantly. |
Fragmented Data Architecture and Engines Create Complexity and Vendor Lock In Legacy Falcon for Endpoint uses different databases and requires architecture changes to move data into LogScale, resulting in messy to little normalization. An antiquated approach tries to mimic SIEM with limited results. |
| AI |
AI-Powered Real-Time Protection With Purple AI from SentinelOne, you can leverage an embedded AI that works in real time, requires fewer updates, and enables you to create generative AI workflows. |
Chatbots That Don’t Enhance Protection On-device AI is weak and ineffective. What’s more, signatures and rulesets require many updates to operate smoothly. Limited Chatbot integration per product creates siloed workflows and does not add any detection or protection benefits. |
Human-Based Detection and Response Charlotte AI is effectively vaporware—no autonomous AI means all detection is service dependent and rule-based detection requires constant updates. |
| Intelligence |
World-Leading Threat Intelligence and Spatial Intelligence Threat intelligence, as well as Google’s advanced threat intelligence, are baked into the platform. PinnacleOne risk advisory delivers high impact geopolitical intelligence to make sure you see the big picture and have a comprehensive security strategy. |
Limited Threat Intelligence Built-in threat intelligence is often insufficient, requiring additional tools and services for comprehensive protection. This fragmented approach can leave gaps in security and make it harder to develop a cohesive threat strategy. |
Legacy IOC Based Threat Intelligence Separately-sold threat intelligence is designed to generate revenue and delivers comic book attribution data that is of no real value. |
| Cloud |
Most Awarded Cloud Security Platform Cloud native and agentless, the SentinelOne Singularity™ Platform delivers real-time protection with no kernel level access, minimizes disruption, and leverages robust performance controls. It also covers public, private, hybrid, and on-premises environments as well as any workload, including serverless. |
Limited Cloud Security Capabilities Microsoft Defender for Cloud lacks verified exploit path prioritization as well as detection of credential leakage in repositories, relies on agents for Kubernetes security, and doesn’t offer shift-left security integration with version control platforms. |
Patchwork of Acquisitions and Legacy Tech That Doesn’t Scale to the Cloud A kernel-based approach is not only not scalable, it’s also a nonstarter when it comes to deployment. Other acquisitions are not integrated and distract from the core offering. It also fails to provide AI-based runtime protection, with coverage limited to classic workloads only. |