N is what’s next
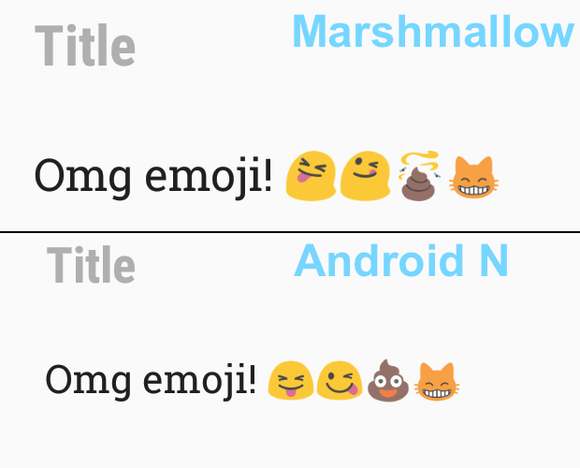
The second developer preview of Android N is here. At first blush, it looks a lot like Android 6.0, Android Marshmallow. But beneath that layer of familiarity, you’ll find lots of little tweaks and improvements to Google’s mobile operating system. It’s early going for Android N, and a lot may change between now and the final release, but let’s dig in and take a look at some of what this new OS has to offer.

Android N: Name TBD
So far, Google isn’t dropping any hints of what tasty moniker it’ll ultimately attach to Android N, or what version number it’ll receive. The final Easter Egg is also still in the works, but if you really want, you can view the placeholder N Easter Egg: Go to Settings > About phone, then tap the Android version repeatedly until a stylized “N” logo appears. Press the N icon repeatedly, and a game of Flappy Android will eventually appear, but it’s the same one that’s in Android Marshmallow.
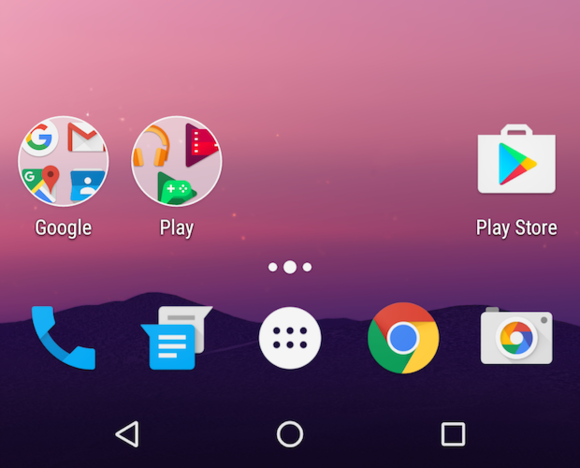
New homescreen folder icons
It’s a little thing, but the homescreen folder icons got a minor visual refresh in Android N Preview 2, with app icons appearing in a grid instead of the stack-of-icons look in Marshmallow. The change is purely cosmetic, though—folders act the same as they did before.
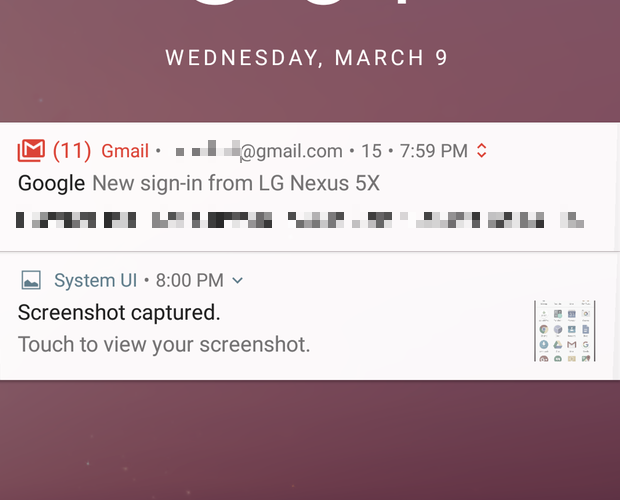
Notifications get an overhaul
The first big change you’ll likely notice about Android N is its redesigned notifications. They look more streamlined, but they actually provide more details, such as the name of the app a notification belongs to. Tap the downward pointing arrow to view a preview or more details (where supported), or tap and hold a notification to adjust how notifications for that app will appear.
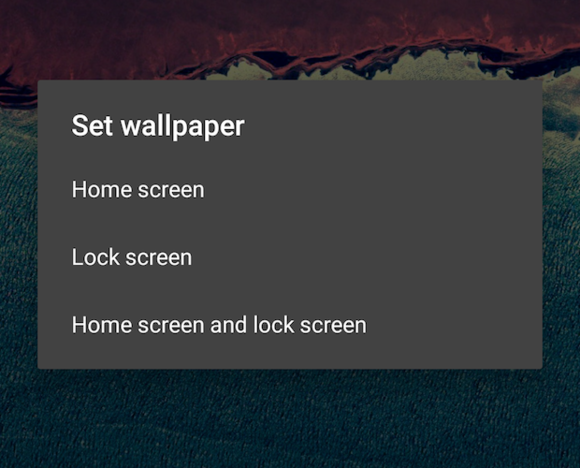
Set a different photo for the lock screen
Change it up a little! With Android N Preview 2, you can now set two different background photos for your home screen and lock screen. For example, you can now have a photo of your cat on your home screen and one of your dog on your lock screen. Go to Settings > Display > Wallpaper, pick your new wallpaper, then tap Set wallpaper as you normally would, then select where you’d like to use that image.
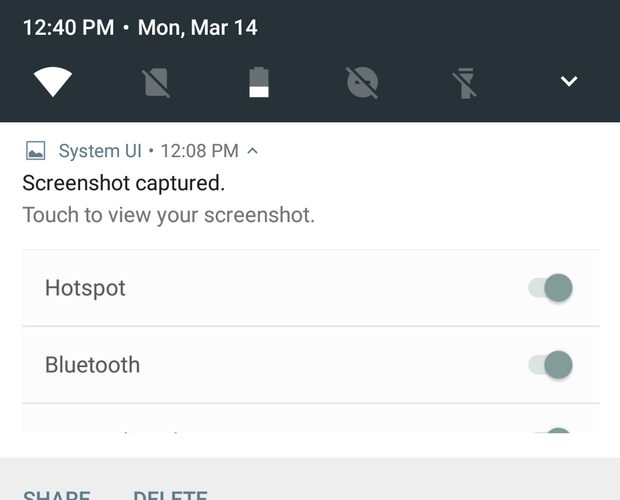
Even quicker Quick Settings
On Android Marshmallow, you had to swipe down from the top twice to get to the Quick Settings drawer (once to open the Notifications drawer, the second time to get Quick Settings to slide down). The Quick Settings drawer is still there in Android N, but you can now get to a handful of important settings from the Notifications drawer itself. One swipe gets you access to battery information, Do Not Disturb, the flashlight feature, and Wi-Fi settings, to name a few. You can choose which five settings go here by re-ordering the Quick Settings—the first five appear here.
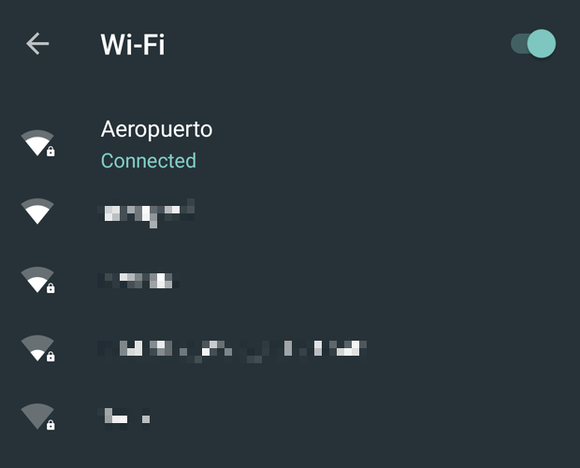
New Wi-Fi network picker
A new, more straightforward Wi-Fi network picker lets you switch Wi-Fi on and off or connect to a network quickly and easily without jumping into the Settings app. Open the Quick Settings drawer then tap the Wi-Fi button to pull it up.
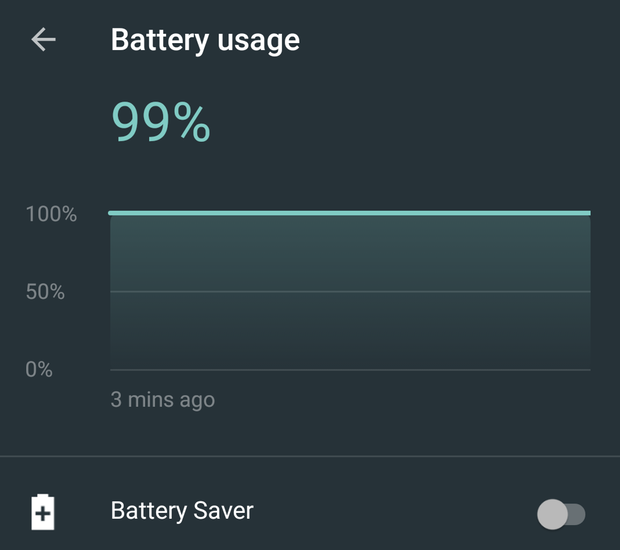
battery saver switch
You can now turn on Battery Saver mode at any time from the Notifications/Quick Settings drawer: Slide down the Notifications drawer, tap the battery icon, then toggle Battery Saver to the On position. You’ll even get a handy chart that shows how quickly you’re draining your battery.
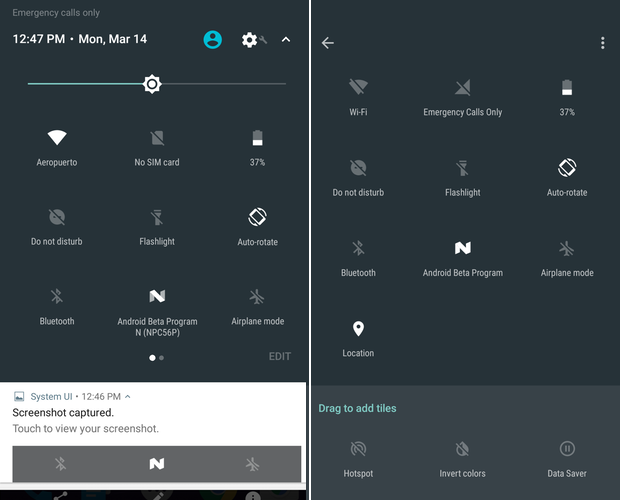
Editable Quick Settings
Android Marshmallow has a hidden feature that lets you edit or rearrange the Quick Settings drawer, but Android N turns this on by default. Simply slide open the Quick Settings drawer, then tap Edit. You can rearrange, add, and remove tiles as you please, simply by dragging them around.
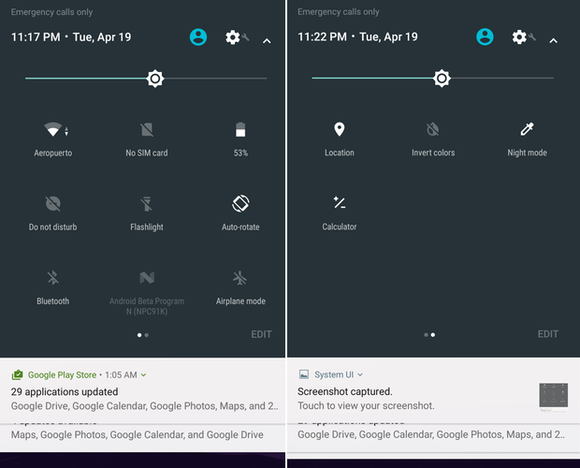
Multiple pages in the quick settings drawer
At first glance, the full quick settings drawer appears mostly unchanged in Android N, but you can now add multiple pages of quick settings icons—useful in case you just want quick access to as many settings as possible.
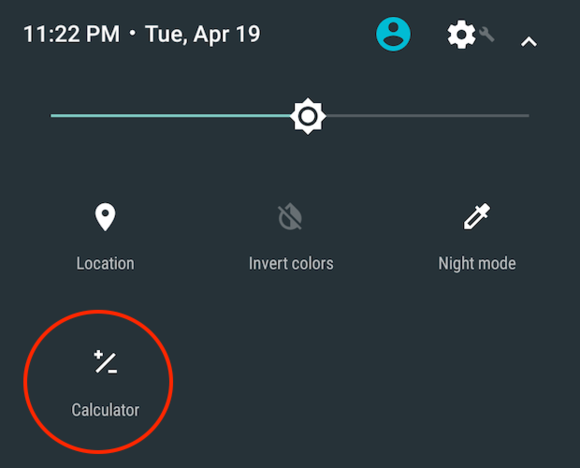
Quick access to the calculator
You can now figure out how much to tip your waiter more quickly and easily than before. An optional Quick Settings tile now lets you pop open the Calculator app from just about anywhere on your phone.
Open the camera app from anywhere
Here’s a handy tip spotted by Android Police : You can open the camera app simply by tapping and holding the Flashlight button in the Quick Settings drawer. Hold it for a second or two, and release your finger once the Camera app opens. A dedicated Camera button would be ideal, but this tap-and-hold trick is the next best thing.

The app drawer lives on
Some time back, the Internet worked itself into a tizzy over buzz that the app drawer may disappear in Android N. We’re pleased to report that the app drawer is alive and well in the Android N preview. (It looks ever so slightly different in Preview 2, but it works the same as it does in Marshmallow.) Whether it appears in the final release of Android N is anyone’s guess, but for now, it’s still there.
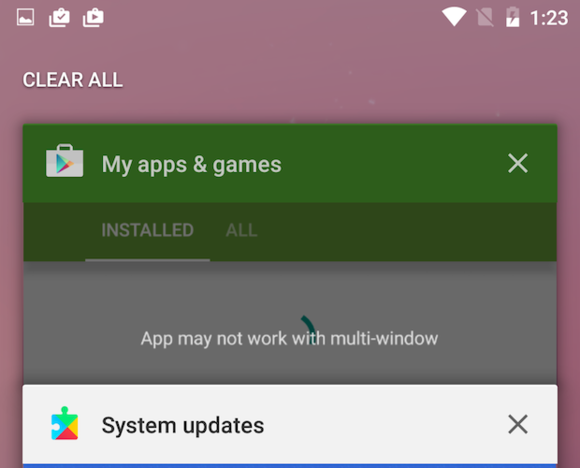
Close all recent apps
Is your app switcher getting a little overcrowded? In Android N Preview 2, you can now close all recently used apps with just a tap. Tap the Recent apps button (the square button at the bottom of the screen), scroll all the way to the top, then tap Clear all.
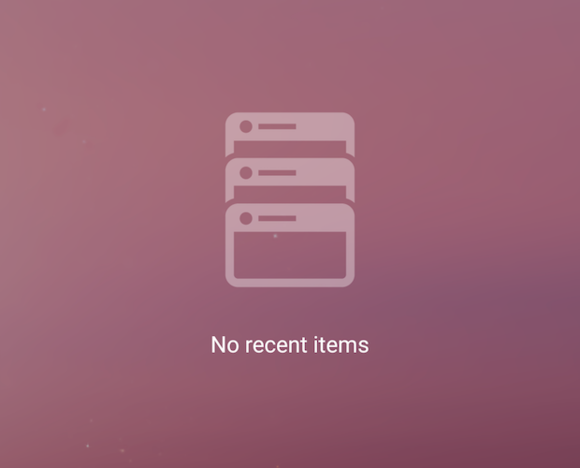
No recent apps
If you have no recent apps to display, Android N Preview 2 will now tell you as much with an icon and message.
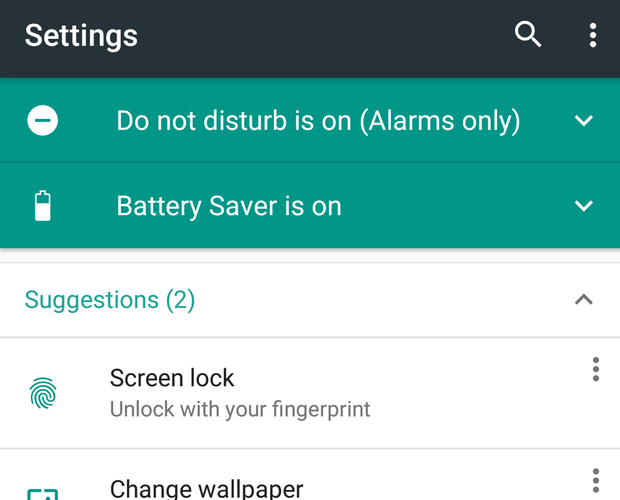
Rejiggered Settings app
The main screen in the Settings app gets an update in Android N. The top of this screen will now provide useful status information about your device (for example, it’ll tell you if you have Do Not Disturb or Battery Saver turned on), and it’ll suggest settings for you to tweak.
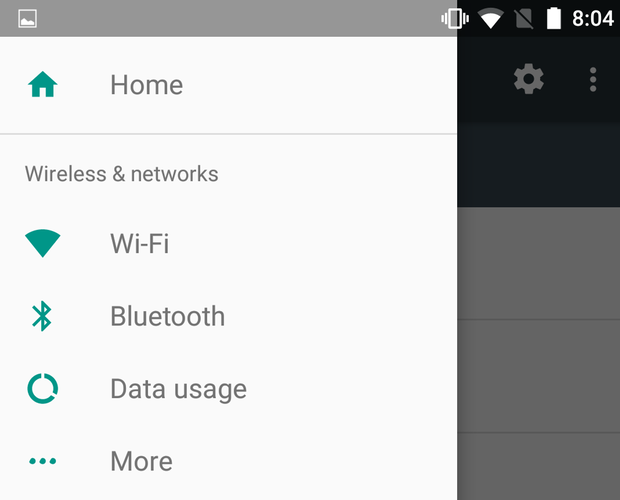
Jump around the Settings app
A new “hamburger” menu lets you switch to any section in the Settings app without returning to the main screen first. It won’t necessarily save you a tap, but it might feel that way.
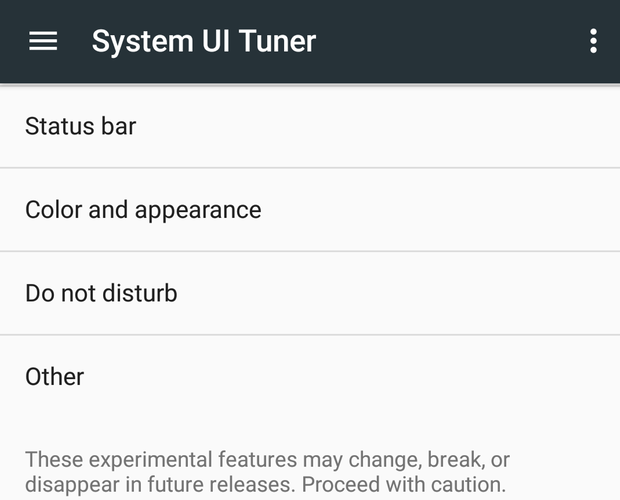
System UI Tuner brings a new batch of tricks
Like Marshmallow before it, Android N includes hidden System UI Tuner options in the Settings app, which lets you toggle a handful of experimental features that aren’t quite ready for public consumption. To turn it on, open the Quick Settings drawer, then tap and hold the gear icon until the icon spins and your phone vibrates. System UI Tuner tools live at Settings > System UI Tuner.

Night mode saves your eyes
Research suggests that exposure to blue light—like the light emitted from computer and phone screens—too close to bedtime can disrupt your sleep patterns, which in turn can lead to a whole host of health problems. But a hidden, experimental Night mode gives your screen a reddish hue, potentially mitigating the effects of this blue light on the body. You can set your phone to switch on night mode automatically, and you can even choose to use a dark theme instead of Android N’s standard black-text-on-white look. Go to Settings > System UI Tuner > Color and appearance > Night mode to give it a try.
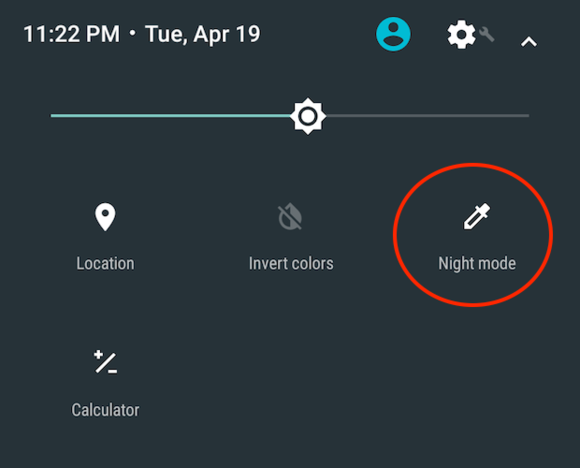
Turn on Night Mode from anywhere
Though Android N’s night mode is very experimental in Preview 2, you can now add a Night Mode toggle to the quick settings drawer. Only time will tell if Night Mode makes it into the final build of Android N.
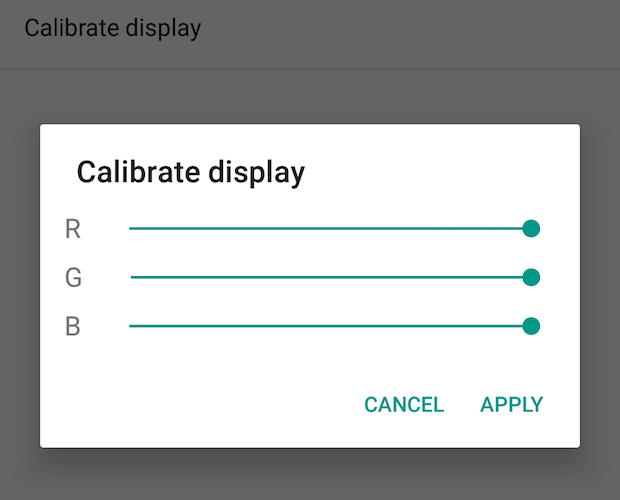
Calibrate your screen
A new, experimental feature lets you adjust your screen’s color balance and white point—useful if you want to manually tweak your screen’s settings so it always looks its best. Go to Settings > System UI Tuner > Color and appearance > Calibrate display, then adjust the red, green, and blue (RGB) sliders as you please. Unfortunately, your screen may not reflect your changes as you make them, so you’ll have to go through a process of trial and error to get things the way you want them.
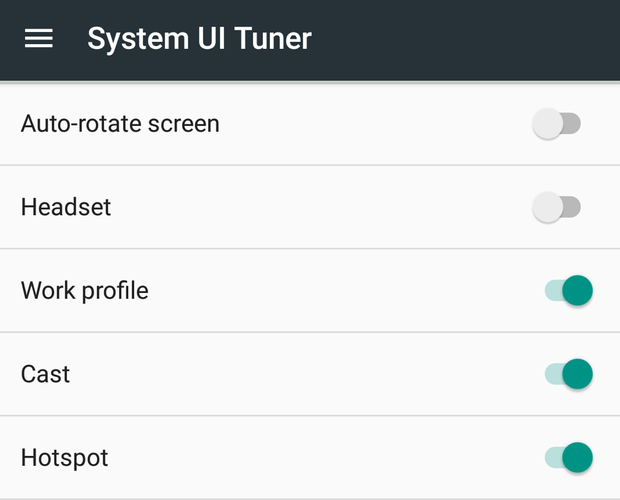
Tweak the status bar
Another System UI Tuner goodie lets you choose which icons—like the battery or Wi-Fi indicators—appear in the status bar.You can also choose to view more (or less) battery status information, or include seconds on the clock. Try it at Settings > System UI Tuner > Status bar.

Split-screen view lets you use two apps at once
Many smartphones have massive screens, and what better way to take advantage of all that space than to view two apps at once? A new split-screen view in Android N lets you do just that without relying on a phone maker’s custom interface. Go to the app switcher, tap and hold an app’s “card” for a moment, then drag it to either the top or bottom of the screen. Next, tap the second app you want to view in this two-up view. You can drag the divider around to resize each app’s usable space, too. To revert to one-up view, simply drag the divider off the bottom of the screen.
Drag and drop text between split-screen apps
You can also drag and drop text between apps when using the split-screen view in lieu of copying and pasting. Simply select the text you want to copy to the other app, then drag it over to the other app with your finger. You need to use your phone in landscape view to get this to work; otherwise, the keyboard can get in the way. According to Android Police, drag-and-drop image support is baked in, but developers will have to update their apps to take advantage of it.
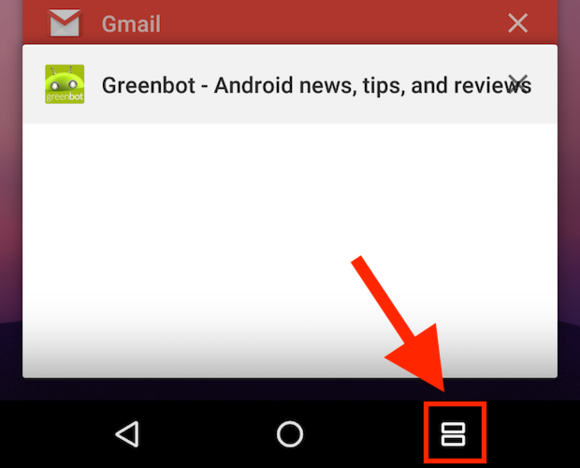
Press button, switch to split-screen view
Here’s another method to switch to split-screen mode: While you’re in an app other than the home screen, press and hold the Recent apps button for a couple seconds. Next, pick the second app you want to use in split-screen mode.